firewall as a service (FWaaS)
What is firewall as a service (FWaaS)?
Firewall as a service (FWaaS), also known as a cloud firewall, is a service that provides cloud-based network traffic analysis capabilities to customers as part of an overall cybersecurity program. FWaaS is a good strategy for organizations seeking to decommission or augment their existing network firewall appliances. It reduces demands on on-premises data center equipment and requires less management time from internal cybersecurity teams.
FWaaS vendors differentiate their service offerings with advanced network security features. These include going beyond traditional network traffic inspection to include next-generation firewall (NGFW) capabilities, such as deep packet inspection and zero-trust network access. FWaaS vendors commonly provide intrusion prevention systems, as well as intrusion detection systems, application-aware security policy enforcement, URL filtering, threat intelligence, and advanced ransomware and malware prevention capabilities.
Artificial intelligence resources can further enhance a firewall's ability to identify suspicious and potentially damaging network traffic. Such advanced capabilities help prevent cyberattacks and other malware from causing breaches and data loss.
How does FWaaS work?
FWaaS operates in a manner similar to any other cloud infrastructure service. FWaaS vendors stand up data centers with massive firewall implementations, achieving significant economies of scale. They then create virtual isolation between the services offered to different customers, avoiding security issues that might arise if one customer were able to modify another customer's configuration or inspect their network traffic.
This article is part of
The complete Secure Access Service Edge (SASE) guide
Each customer is assigned a virtual instance of the FWaaS service that they may modify through a centralized console or dashboard. Vendors typically use the firewall configuration interfaces already familiar to cybersecurity teams. In fact, customers moving from an on-premises firewall appliance to FWaaS offered by the same vendor might be able to use the same management interface they had been using for their on-site devices and endpoints.
The cybersecurity team first configures the firewall rules and other settings that implement the organization's security policy. It then modifies network and domain name system settings to flip the virtual switch, routing traffic through the FWaaS vendor's infrastructure for security policy enforcement. At that point, the FWaaS service replaces existing network perimeter configurations as the first line of defense.
Figure 1 depicts a traditional firewall installation, with the firewall located in a data center or network operations center as the first line of defense in the network perimeter.
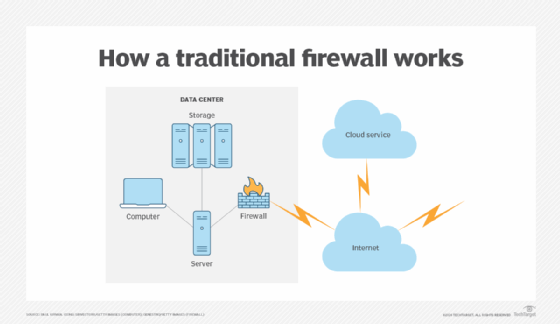
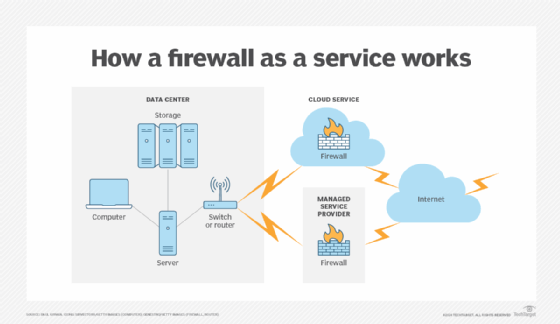
Figure 2 presents a FWaaS configuration with the virtual firewalls housed in either a cloud service provider or a managed service provider facility. The network perimeter now extends to the third-party FWaaS vendor.
Why is FWaaS important?
FWaaS platforms are playing an increasingly important role in cybersecurity programs due to the following three factors:
- Organizations have been adopting cloud-first strategies where they seek to outsource infrastructure, software and other services to cloud providers as much as possible.
- Traffic originating outside the organization can remain in the cloud, bypassing on-premises data centers and communications links for remote and mobile users. This reduces network latency and other issues that can affect local equipment performance.
- Offloading a major security service to a cloud provider enables internal resources to focus on other activities.
Advantages and disadvantages of FWaaS
Organizations weighing a potential move to a FWaaS offering might wonder whether the timing is right for such a move. Consider the following advantages and disadvantages of these products:
- FWaaS offerings provide scalability, enabling vendors to spread the cost of enhanced service offerings across many clients. However, service providers can also raise their rates. Depending on the specifics of any contract, the net financial effect of a move may be insignificant or could even increase direct costs.
- Adopting a FWaaS product enables an organization to gain access to state-of-the-art security filtering technology. Upgrades should occur in a relatively seamless fashion, enabling organizations to draw upon the deep expertise of the vendor as it's often operating its own security solution.
- FWaaS offerings are gathering momentum in the market. While some vendors have offered these services for several years, perimeter protection is a business-critical service. Cybersecurity professionals considering a service offering must be confident that the service is rock solid and doesn't disrupt business operations.
- As organizations move significant portions of their operating environment to the cloud, FWaaS provides the benefit of cloud-native firewalls. These offerings incorporate cloud capabilities as baseline features, enabling teams to quickly secure their cloud applications and operations.
- IT teams must be certain their firewalls are secure and don't share traffic with other customers; they must also be certain that cloud security personnel are trustworthy and not likely to spy on or steal data traversing firewall services.
FWaaS and SD-WAN
FWaaS service offerings integrate well with software-defined wide area network (SD-WAN) strategies that seek to decentralize network traffic routing. SD-WAN's dynamic route optimization capabilities make it difficult to use traditional network firewalls, which quickly become a chokepoint.
FWaaS allows the firewall to exist as a cloud-based service, reducing the dependency on the enterprise network. The service also scales efficiently as the volume of traffic traveling over each customer's network varies. Together, FWaaS and SD-WAN are two foundational components of the network security strategy known as secure access service edge, or SASE.
FWaaS vendors
Vendors across the security spectrum have cloud-based FWaaS solutions. The major cloud infrastructure vendors -- Amazon Web Services, Google and Microsoft -- all provide cloud-based firewall capabilities for their own environments and also offer NGFW service functionality for on-premises traffic. Some of the major players in the market are traditional firewall vendors, such as the following sampling:
- Barracuda Networks.
- Cato Networks.
- CheckPoint.
- Cisco.
- Fortinet.
- Juniper.
- Netgate.
- Palo Alto Networks.
- SonicWall.
- Sophos.
- WatchGuard.
- Zscaler.
Learn more about the security features and benefits offered by FWaaS.







